Crypto keyring dmvpn vrf dmvpn pre shared key address 0 0 0 0 0 0 0 0 key cisco when you are using a front door vrf you can t define the key using the old crypto isakmp key command.
Bgp front door vrf.
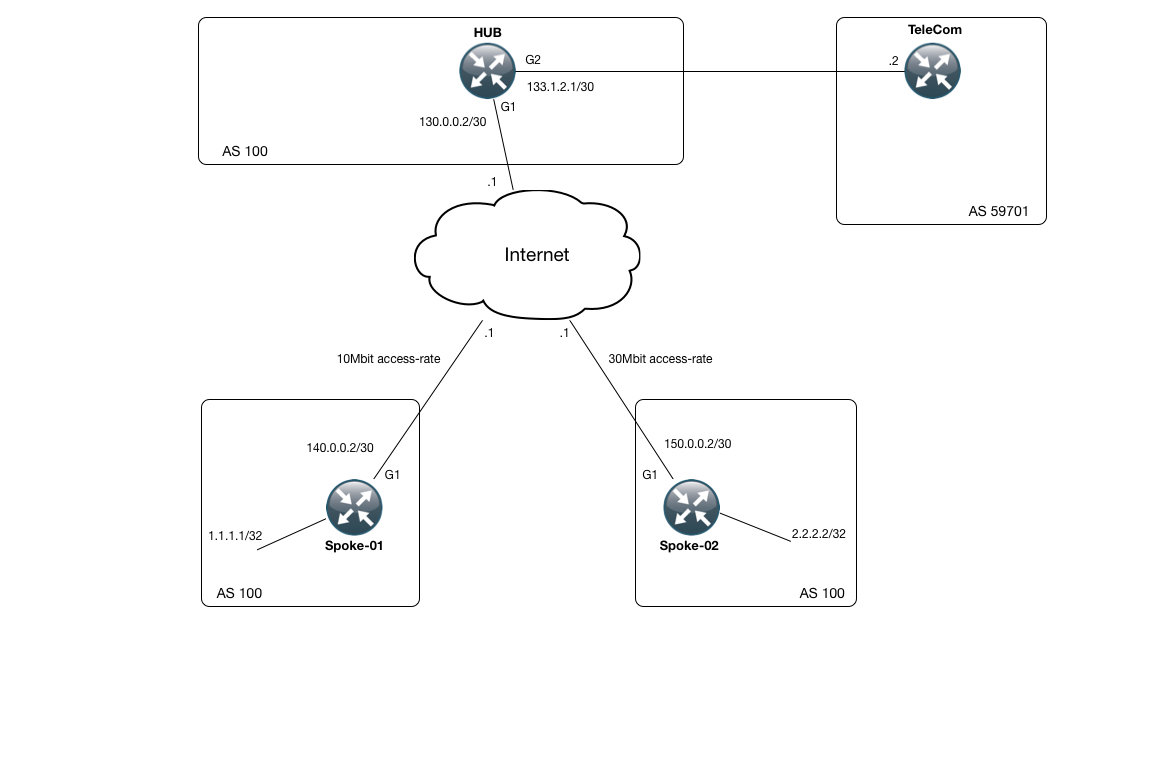
In order to understand the use of front door vrfs let us use a simple topology as below where we will create a simple gre tunnel between r1 and r4.
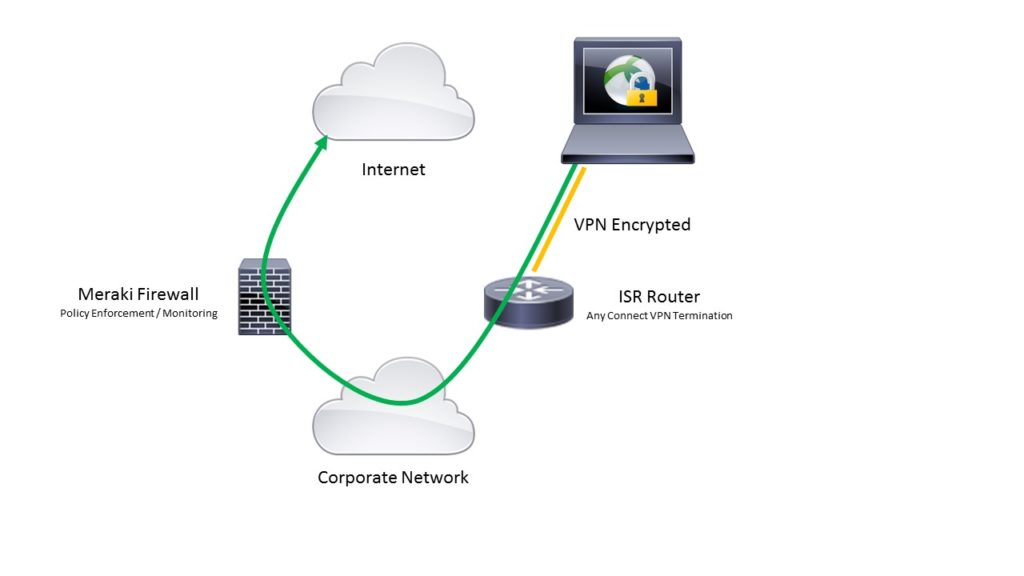
The outer encapsulated packet belongs to one vrf domain called the front door vrf fvrf while the inner protected ip packet belongs to another domain called the inside vrf ivrf.
Stated another way the local endpoint of the ipsec tunnel belongs to the fvrf while the source and destination addresses of the inside packet belong to the ivrf.
Ip route vrf front door 0 0 0 0 0 0 0 0 z z z z you have to tell the tunnel interface to use the new vrf for establishing the tunnel.
Bgp has also been used in the core of large enterprise environments as a tool to enhance network scalability and support separate administrative control domains.
Vrf domain called the front door vrf fvrf while the inner protected ip packet belongs to another domain called the inside vrf ivrf.
This includes things such as the correct tunnel configuration routing configuration using bgp as the protocol of choice as well as nat toward an upstream provider and front door vrf s in order to implement a default route on both the hub and the spokes and last but not least a newer feature namely per tunnel qos using nhrp.
Stated another way the local endpoint of the ipsec tunnel belongs to the fvrf while the source and destination addresses of the inside packet belong to the ivrf the unprotected lan side.
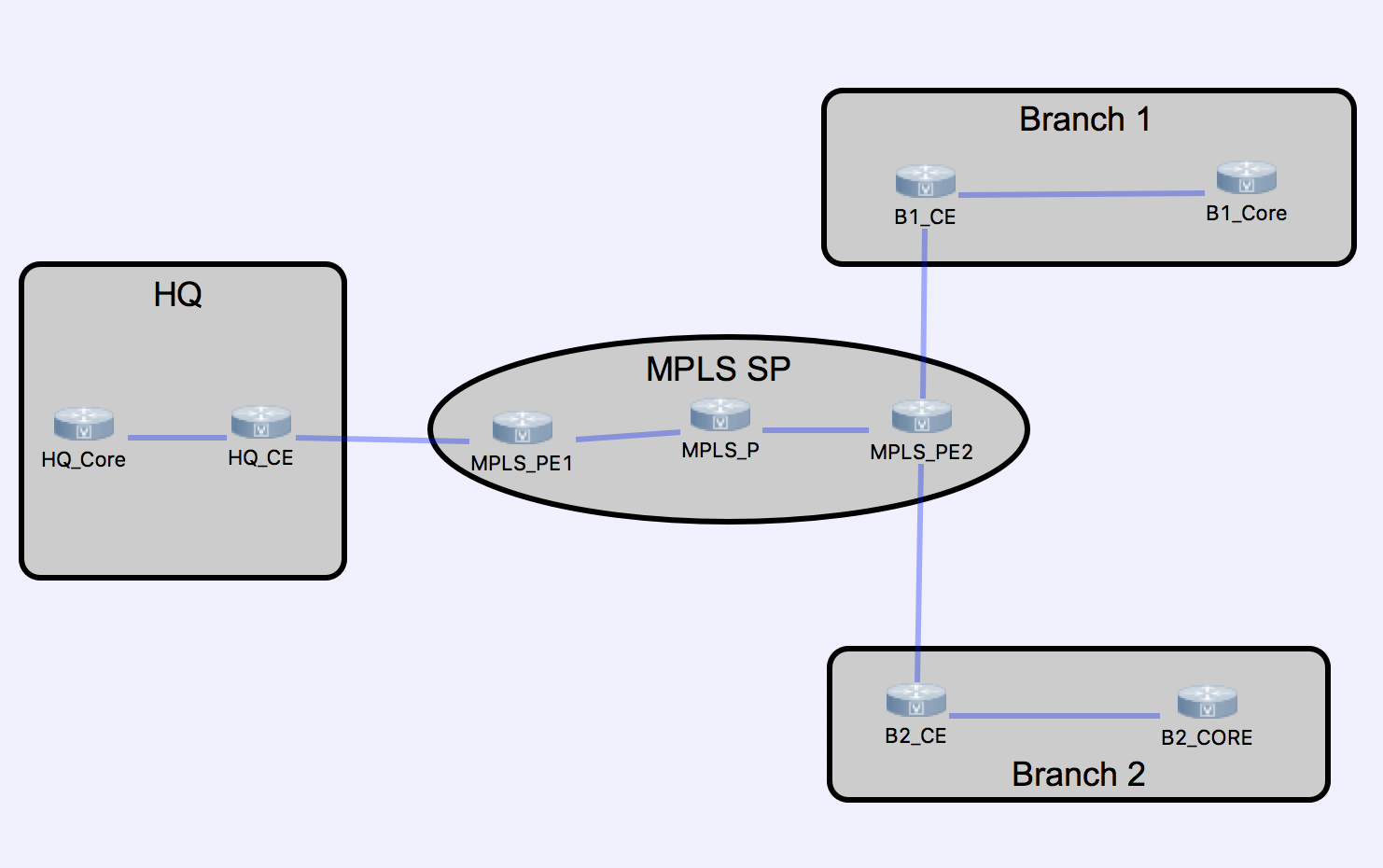
However another way to use bgp in the enterprise is on a single router supporting networking virtualization with vrf lite.
All we did is stitch them together.
Both r1 and r4 will learn about the tunnel destination address via underlying protocol i e.
Ospf in our case.
Router ospf 100 vrf pipe router id 13 13 13 13 4.
On r1 the vrf router remove all the neighbor statements from the parent bgp protocol all statements for the 10 1 1 2 neighbor should be inside the address family ipv4 vrf bgp with the static routes your ping is failing because you are not adding the vrf bgp to your ping command.
As you can see we did not move the tunnel11 interface from the global routing table to the routing table for vrf pipe.
The key must be defined in a keyring.
Vrf lite is also known as multi vrf.
I just did your topology on a lab and had 0 issues.